The student portal of San Beda University was hacked last June 4, 2020, according to an article published by Rappler. Hackers behind the attack are still unknown. The university has yet to release any statement as of this writing.
Per initial reports, San Beda’s student portal was defaced to get the attention of school’s officials. It looks like the hackers involved in this security incident may have been in contacts with the school. The defacement could just be a proof to let the school know that they are serious about their claims. The compromised student portal has since been taken down. Students used to access the portal to check for their grades.
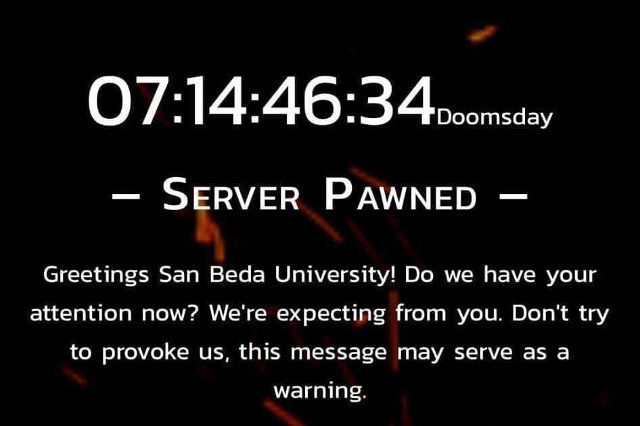
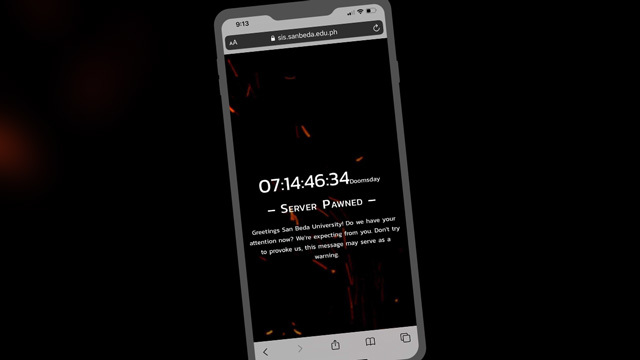
The culprits posted this message on the defaced website: “Server Pawned. Greetings San Beda University! Do we have your attention now? We’re expecting from you. Don’t try to provoke us. This message may serve as a warning.” This is accompanied by a doomsday timer which will end in 7 days.
They also managed to hack the FB Page for Admissions Center of San Beda University where they also posted the same message.
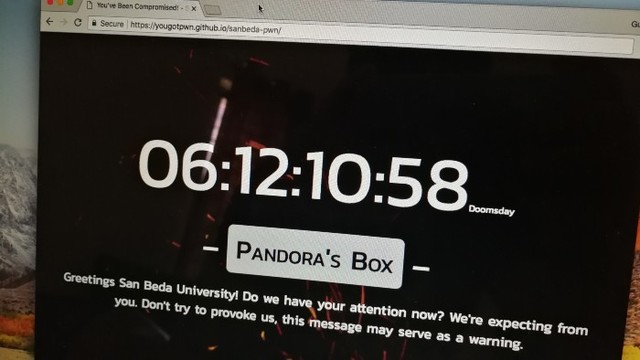
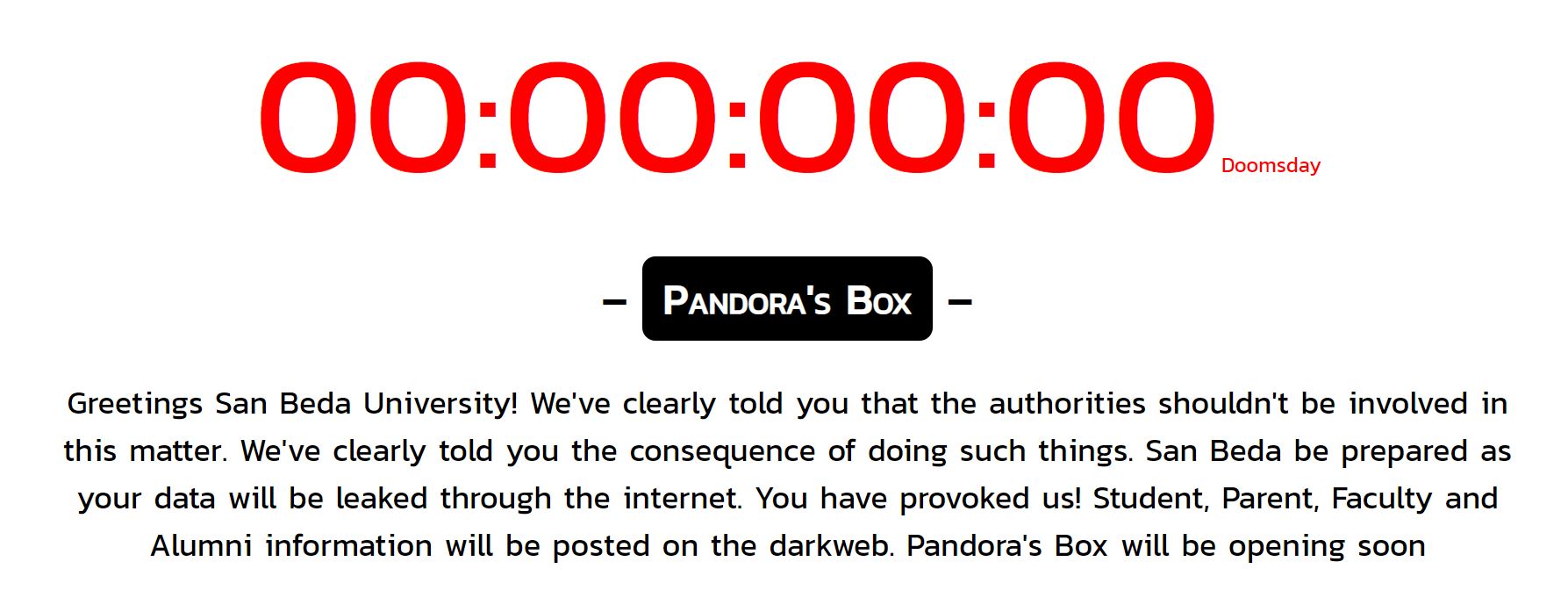
On June 5, the hackers moved their warning page to GitHub and added a clickable Pandora’s Box button. By the looks of it, this button could lead to a page where the hackers keep the database that they may have obtained.
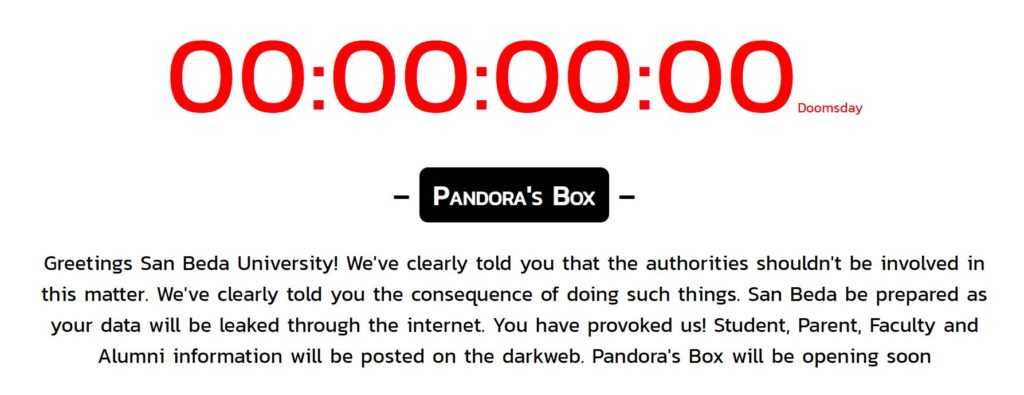
On June 6, the hackers updated the warning page in GitHub. The timer was set to 00:00:00:00 indicating that they are about to open the Pandora’s Box. This is even if the original doomsday counter says that the school has 7 days to do whatever the hackers are asking them to do. According to the pop up message that appears when you click on the button, the database will be opened anytime today, June 7.
The message was also changed with more information about what could’ve happened to the student portal. Based on the updated GitHub page, San Beda’s student portal has been logging all errors which contain user credentials in clear text format. This allowed the culprits to get hold of a whopping 400,000 user log ins between 2019-2020. They even went on providing evidence that they do have the credentials of the students, parents, faculty members and alumni who have accessed the portal within the mentioned duration.
The hackers are to leak this database publicly anytime today. It seemed like that they were pissed off with how the school officials treated their earlier warnings. The hackers may have been asking for a ransom for the information that they have and would like to keep the negotiation between them only. San Beda may have involved the authorities in the incident which forced the hackers to just leak the database.
San Beda University, like any other institutions in the country, is required to report the incident to authorities and regulatory bodies such as the National Privacy Commission (NPC). For instance, NPC requires institutions to send a breach notification with the agency and to the affected data subjects within 72 hours from the time of discover.
Students and other members of the San Beda University community who have accessed the portal are strongly advised to update their credentials specially if they’re using the same password on their other online accounts such as in social media platforms.
**Updates**
June 7, 2020: San Beda University released a statement saying “the apparent hacker got through the system set up by the third-party company that SBU had hired for their student portal, Princtech Company.” They have also reached out to the National Bureau of Investigation and NPC to probe the breach and other services from the Investigation hotline to help with this as well.
Photo Credits: Rappler.com
- PH releases first Super App ‘eGov PH’ - June 3, 2023
- Finding the Best Place for Repairs After a Car Accident - February 27, 2021
- ABS-CBN YouTube channels hacked by crypto scammers - November 4, 2020