Just when you thought that the government is already taking online security seriously after the growing number of website defacement and data breach incidents recently, it seemed like they’re still not ready to face these threats yet.
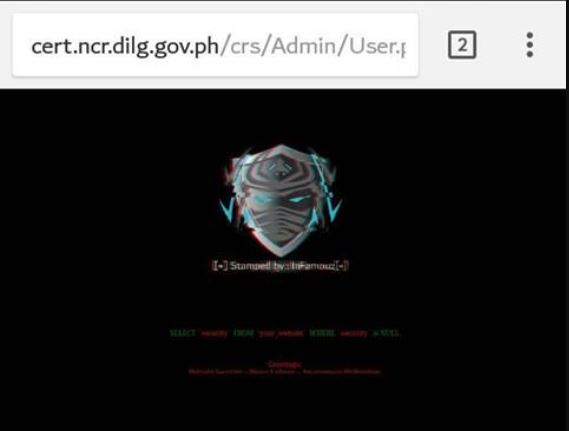
In a report sent to us, a hacker managed to deface the website of the Department of Interior and Local Government – National Capital Region (DILG-NCR) particularly their Web Portal under the subdomain cert[.]ncr[.]dilg[.]gov[.]ph.
The said Web Portal contains log-in links to the agency’s multiple systems including Design Monitoring System, Records Databank System, Records Registry Tracking System, and Certificate Registration System.
It’s confusing why these systems are located under this subdomain when CERT generally stands for Computer Emergency Response Team. The Web Portal, which is hosted under this cert subdomain, does not seem to connect with the mandate of a CERT.
According to Section 4 of Executive Order No. 189, s. 2015, all bureaus, offices, agencies, and instrumentalities of the government were mandated to organize their respective CERTs. The compromised DILG-NCR subdomain may have been set up to be an online CERT portal for the agency.
If this is indeed the CERT portal of the agency, isn’t it ironic that it was hacked when the purpose of its creation is to prepare “appropriate and effective measures to strengthen their cybersecurity capabilities against existing and future cyber threats”?
Our source said that he merely did a script deface or javascript overlay to deface the DILG-NCR website. But being the ‘good guy’ that he claimed to be, this attack was just to push the agency to act and secure their own website.
Based on the screenshot provided in the report, the culprit behind this attack is InFamouz, the grayhat hacker we featured a couple of days ago known for his attempts to compromise websites and deploy the appropriate patches afterward.
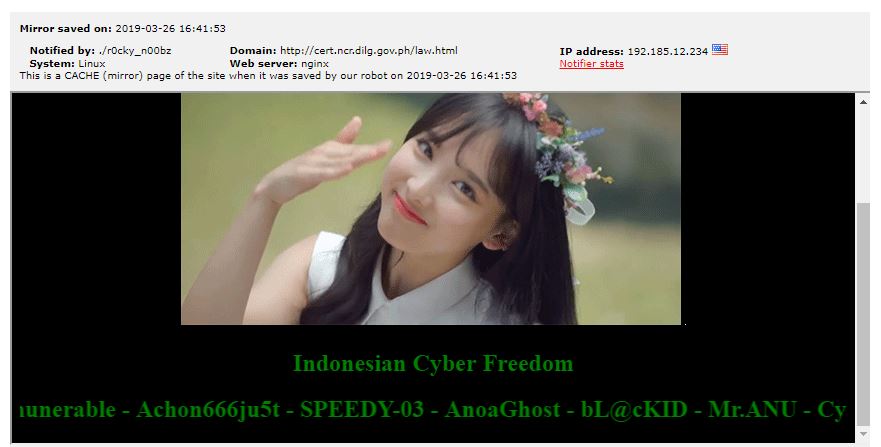
It can also be remembered that this same domain has been compromised almost a month ago by hackers presumably from Indonesia. Zone-H records show that it was defaced back on March 26, 2019.
We will have this coordinated with DILG-NCR and with the National Computer Emergency Response Team for proper actions.
- Phishing Email Analysis Landing Page - September 19, 2024
- BPI to hold Cybersecurity Conference to ‘Fortify Cyber-Resilience in an AI World’ - July 25, 2024
- New Smishing Campaign makes use of Globe SMS Sender ID - May 27, 2024
